The internet has revolutionized the way we communicate, access information, and conduct business. However, with the increasing reliance on the internet, we are also faced with the risk of internet intrusion, or the unauthorized access or interference with computer systems or networks.
One type of internet intrusion is cybercrime, which refers to criminal activities that are committed using the internet or other forms of digital communication. Cybercriminals may use various techniques, such as malware, phishing, or ransomware, to gain access to computer systems or steal sensitive information, such as passwords, financial data, or personal identification. Cybercrime can have serious consequences, including financial loss, identity theft, and damage to reputation.
Another type of internet intrusion is cyber espionage, which involves the use of the internet to gather sensitive information for strategic or competitive advantage. Governments, militaries, and businesses may engage in cyber espionage to gain access to intellectual property, trade secrets, or confidential communications. This type of intrusion can have serious implications for national security and international relations.
A third type of internet intrusion is cyberbullying, which refers to the use of the internet or other digital communication to harass, intimidate, or otherwise harm an individual or group. Cyberbullying can take various forms, such as online harassment, sextortion, or impersonation, and can have severe consequences, including psychological distress, social isolation, and even suicide.
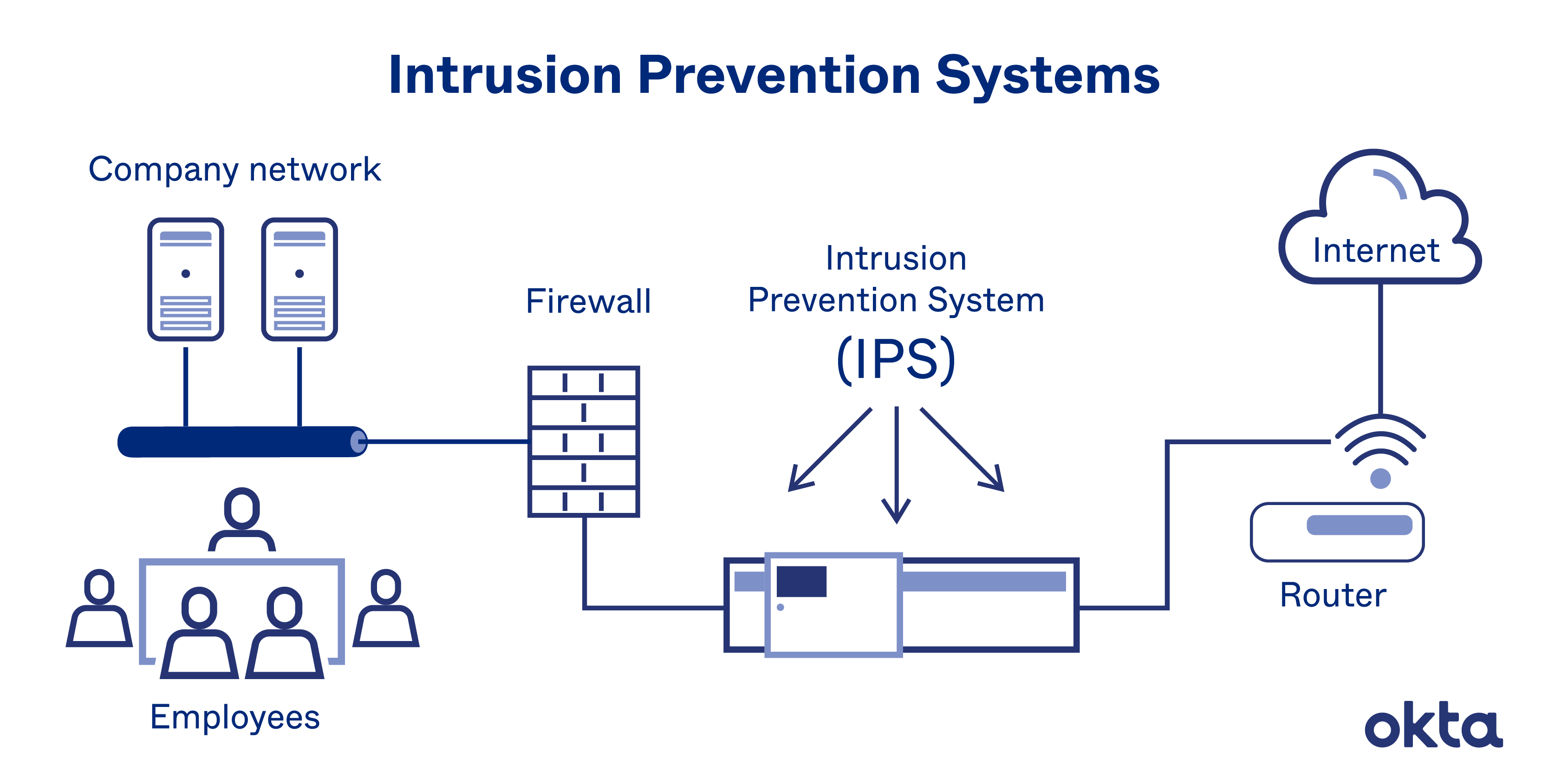
To protect against internet intrusion, it is important to adopt good cybersecurity practices, such as using strong passwords, installing antivirus software, and being cautious about clicking on links or downloading attachments from unknown sources. It is also important to educate ourselves and others about the risks and ways to prevent internet intrusion, and to report any suspicious activity to the appropriate authorities.
In conclusion, while the internet has brought many benefits, it has also opened the door to various forms of intrusion, including cybercrime, cyber espionage, and cyberbullying. To protect ourselves and our organizations, it is essential to adopt good cybersecurity practices and to be aware of the risks and ways to prevent internet intrusion.






.pdf/page1-1200px-Development_of_an_internet_intrusion_prevention_tool_(IA_developmentofint00anun).pdf.jpg)

