Steganography is the practice of hiding information within other, seemingly innocent information. It is a method of covert communication that can be used to transmit messages or files in a way that is difficult for outsiders to detect. Steganography differs from cryptography, which is the practice of encoding messages in a way that makes them unreadable to anyone who does not have the key to decode them.
One common method of steganography is to embed a message within an image file. This can be done by altering the least significant bits (LSBs) of the pixel values in the image. The human eye is generally unable to detect small changes in the pixel values, so the message is effectively hidden within the image.
Another method of steganography is to hide a message within the metadata of a file. Metadata is information about the file, such as the file name, size, and creation date, that is stored in the file itself. A message can be hidden within the metadata by using a key to encode the message and then adding the encoded message to the metadata.
Steganography can also be used to hide messages within audio or video files. In this case, the message is embedded within the audio or video data itself, rather than within the file metadata.
One advantage of steganography is that it allows for the transmission of secret messages without drawing attention to the fact that a secret message is being transmitted. This makes it a useful tool for those who wish to communicate covertly, such as journalists or political dissidents.
However, steganography is not a foolproof method of communication. It is possible for outsiders to detect the presence of a hidden message by examining the file for unusual patterns or by using specialized software to analyze the file. Additionally, the use of steganography can be illegal in some countries, so it is important to be aware of the laws and regulations in your jurisdiction before using it.
Overall, steganography is a useful tool for covert communication, but it is not a replacement for strong encryption techniques. It is best used in conjunction with other security measures to provide an additional layer of protection for sensitive information.
What are the advantage and disadvantage of Steganography?

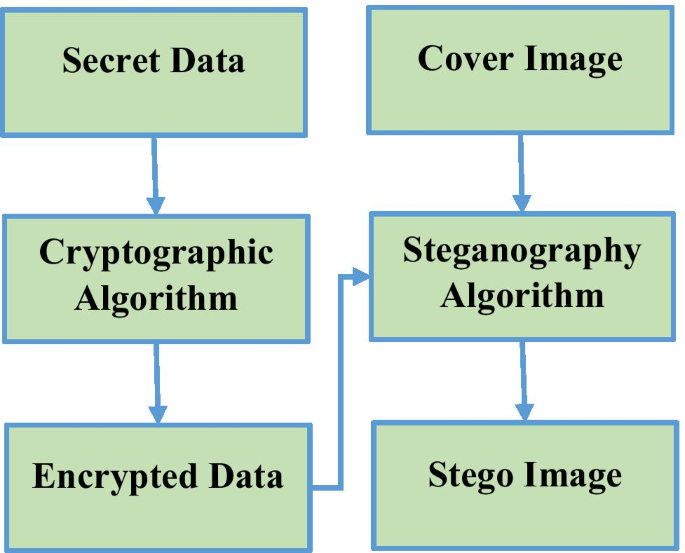
Obfuscation, like steganography, is defined as hiding information, but the big difference is that the former method deliberately makes the message hard to interpret, read, or decode. This is used to transfer some secret message to another person; with this technique, no one else in between will know the secret message you wanted to convey. It makes use of ordinary files like text, audio, image, videos, and even Word or Excel sheets to conceal information. Authentication data is 48 bytes long in total. My practical approach for securing normal computer info is by using the free KeePass with long, complex password, then using its built-in file-storing ability to attach files within its secure framework; once saved, only I can open it, and the little program so far seems hardy and crash-resistant. They hold values to represent the brightness of a given colour at any specific point. However, criminals and terrorist organizations also started using this for their communication.
Steganography

A message, the cover text is modified in some way so as to contain the ciphertext, resulting in the stegotext. After all, we need to stay one step ahead of hackers and would-be data thieves! The result is that the hidden message remains hidden. SilentEye It encrypts your information as well as compresses it. The pre-distributed static public key and private part of the ephemeral key are used to generate a shared secret, with which the Client's secret identifier UID , along with some miscellaneous information such as the reply prevention timestamp , are symmetrically encrypted. If an image block matches the malware, the hackers fit it into the carrier image, creating an identical image infected with the malware. Lecture Notes in Computer Science LNCS 5332, Springer-Verlag Berlin Heidelberg, Proc. Nevertheless, to hide and reveal text inside an image, you need to enter another image as a key.
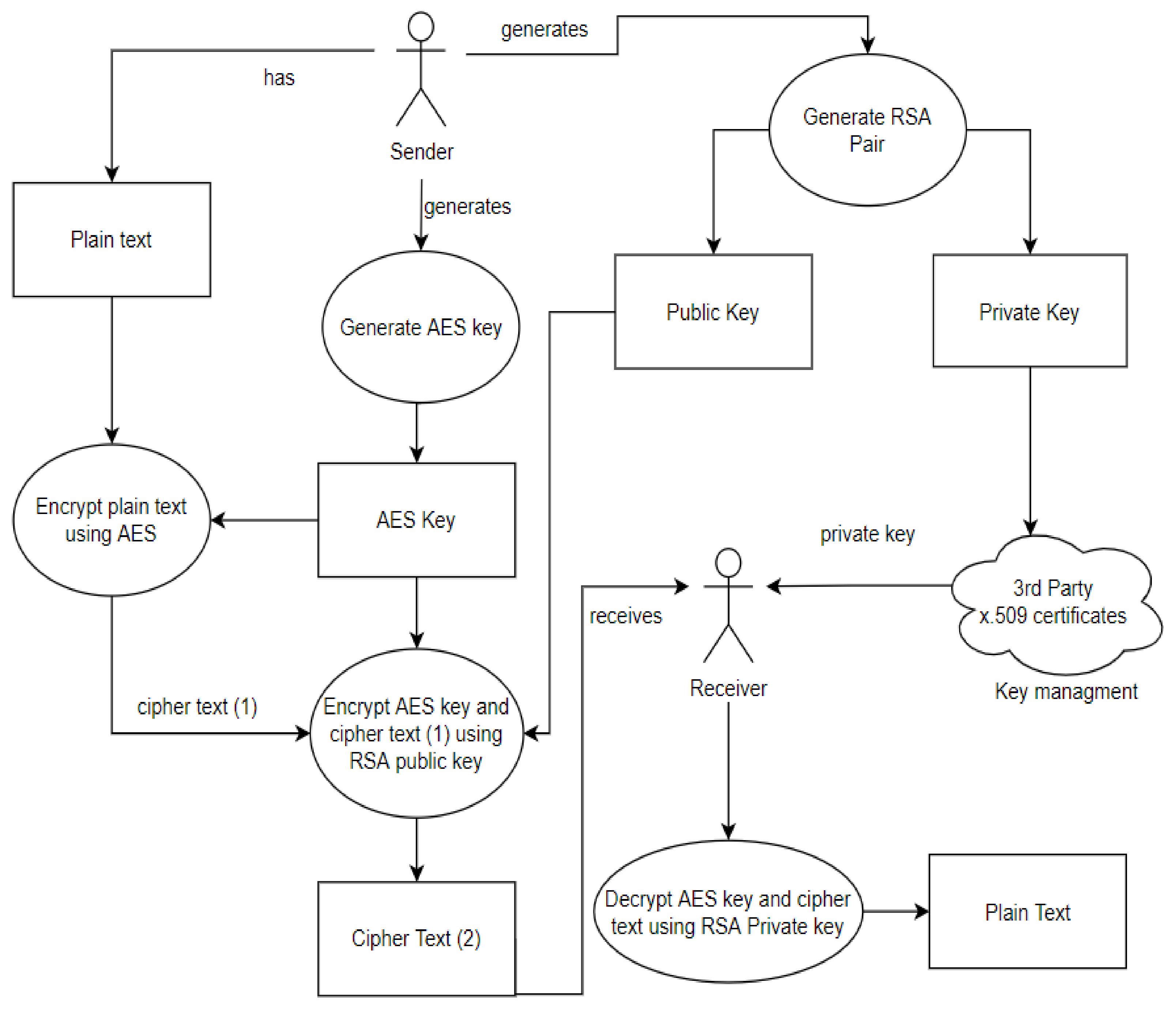
PDF Steganography Using Hybrid Crypto Encryption Technique

The message is useless for them. Video steganography typically employs the following file formats: H. To decrypt the image, just load it on this Steganography tool and input the password, and voila! When a poor, unsuspecting user clocks one of those documents open, they activate the secret, hidden script, and chaos ensues. Retrieved 14 December 2021. What's next for Agent Maverick We hope that we will be able to include an array of encryption methods for the users to choose from to encrypt their secret messages before embedding them into images.