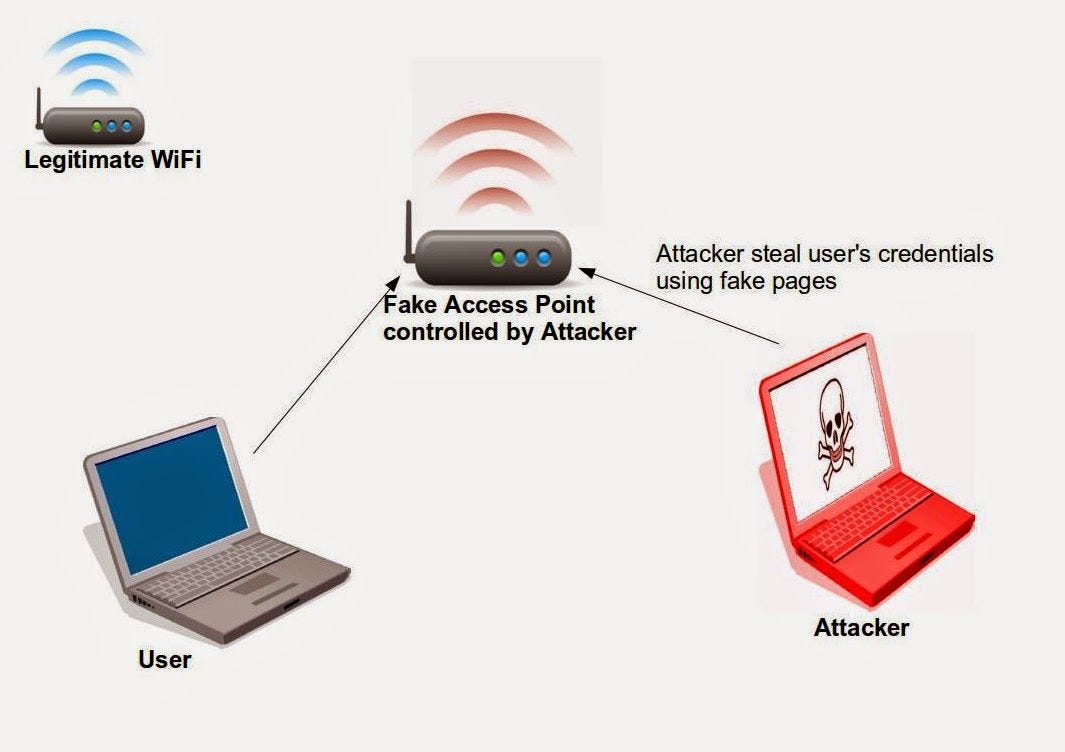
An "evil twin" attack is a type of cyber attack in which an attacker creates a fraudulent wireless access point that looks legitimate to the victim, but is actually used to intercept the victim's data. This type of attack is often used in public places such as coffee shops, airports, and hotels, where people may be more likely to connect to a seemingly trustworthy wireless network.
In an evil twin attack, the attacker first sets up a fake wireless access point with a name and appearance that is similar to a legitimate one. For example, if the legitimate access point is called "Airport WiFi," the attacker may create an access point called "Airport WiFi 2" or "Airport WiFi Free." The victim, thinking they are connecting to a legitimate network, will then enter their login credentials or other sensitive information, which the attacker can then intercept and use for nefarious purposes.
One of the main ways that evil twin attacks are successful is through the use of social engineering techniques. The attacker will often try to make the fake access point seem as legitimate as possible, using tactics such as creating a professional-looking website or using a trusted brand's logo. This can make it difficult for the victim to discern the difference between a legitimate access point and a fraudulent one.
To protect against evil twin attacks, it is important to be cautious when connecting to public WiFi networks. One way to do this is to make sure that the network you are connecting to is actually the one you intended to connect to. This can be done by verifying the network's name and checking for any spelling errors or strange characters. You should also avoid entering sensitive information, such as login credentials or financial information, while connected to a public WiFi network.
It is also a good idea to use a virtual private network (VPN) when accessing the internet on a public WiFi network. A VPN encrypts your internet connection and can help protect your data from being intercepted by an attacker.
Overall, evil twin attacks are a serious threat to individuals and organizations, as they can potentially compromise sensitive information and lead to financial loss or identity theft. By being aware of this type of attack and taking steps to protect yourself, you can minimize the risk of falling victim to an evil twin attack.
What Is an Evil Twin Attack and How Can You Prevent It?
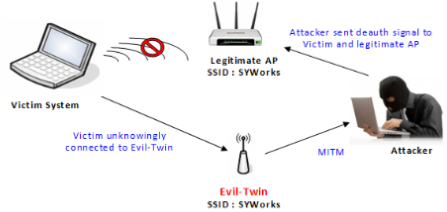
Unfortunately, an evil twin attack is relatively easy to set up and difficult to detect due to the nature of how devices connect to Wi-Fi. What other Wi-Fi security risks are there and will these affect me? This enables hackers to set up malicious APs that can eavesdrop on the traffic and extract sensitive information. With the rapid rise of remote work environments, companies are unwittingly exposing their networks to savvy hackers. Airports, coffee shops, libraries, shopping malls. Additionally, the hacker is able to steal data or plant malware. A tool like dnsmasq can be used to create captive portals and spoof DNS serversto increase the semblance of legitimacy. They can also flood the original connection with a denial of service DoS attack.
Evil Twin in Kali Linux

How an evil twin attack affects you If successful, a hacker has essentially intercepted your internet connection, connecting you to them. This might seem beneficial to them on the surface, but actually, they are exposing themselves to evil twin attacks. In a case where the device has already connected to the legitimate AP. Again, this is a basic step and simply requires the attacker to change the name of the fake hotspot to that of the legitimate one so that when the unsuspecting victim sees it, they do not think anything of it. This means that the script will launch the tools for us using our given settings, as opposed to us having to manually set up each of the tools separately. What is an Evil Twin? Another ploy for evil twin hackers is to move closer to their victims, creating a more Attackers can access live user data, from scrolling through social media accounts to accessing user bank account information.
How to Detect and Attack Evil Twin WiFi Access Points
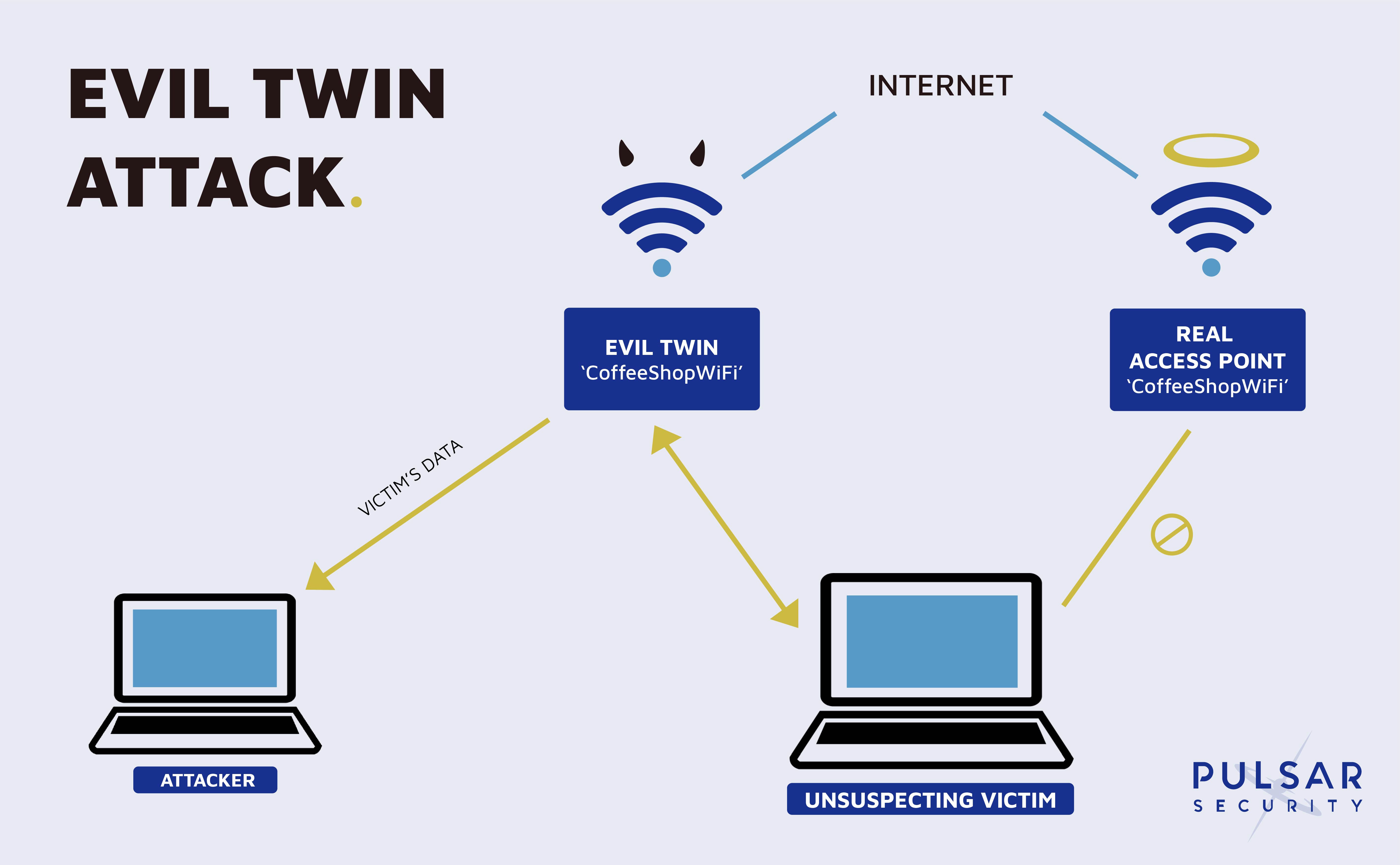
But how safe are these access points, and what risk do they pose to your security? For organizations, this can be extremely concerning if the victim is using a company device or, more commonly, the device is connecting to any app, software, or is accessing any site that could then allow the hacker to infiltrate the organization. I enjoy reading, researching the topics I write, Alabama Football, hunting with my boys, and a daily fitness routine that is always being revised. Task 3: With the initial setup behind us, we can now begin the attack. Hackers will replace or forget to use a single letter in the name, which most people overlook. Employees may connect and log into a company website through a phony WiFi hotspot thinking it is a legitimate access point. Enter your password and return to the script.
Evil Twin Attacks & How our Solution Mitigates Them

They exist in restaurants, coffee shops, and shopping malls. These are the best practices for using public WiFi hotspots. And, in this case, the devices automatically connect to a network with a stronger signal. This can lead to stolen credentials and sensitive information, resulting in identity theft or financial loss. If you find it shocking that a nearly 20 year old Wi-Fi attack is still this effective, you should be! Hotspots are created using the same A Large variety of devices can be used, from smartphones and computers to portable routers and tablets. Heed Security Alerts Some devices and security suites have cyber threat detection features. To increase their odds of success, they can physically move the hotspot or Wi-Fi-emitting device closer to the victims, so the connection appears first and is stronger than the real connection.
Evil Twin Attack: Definition and Prevention
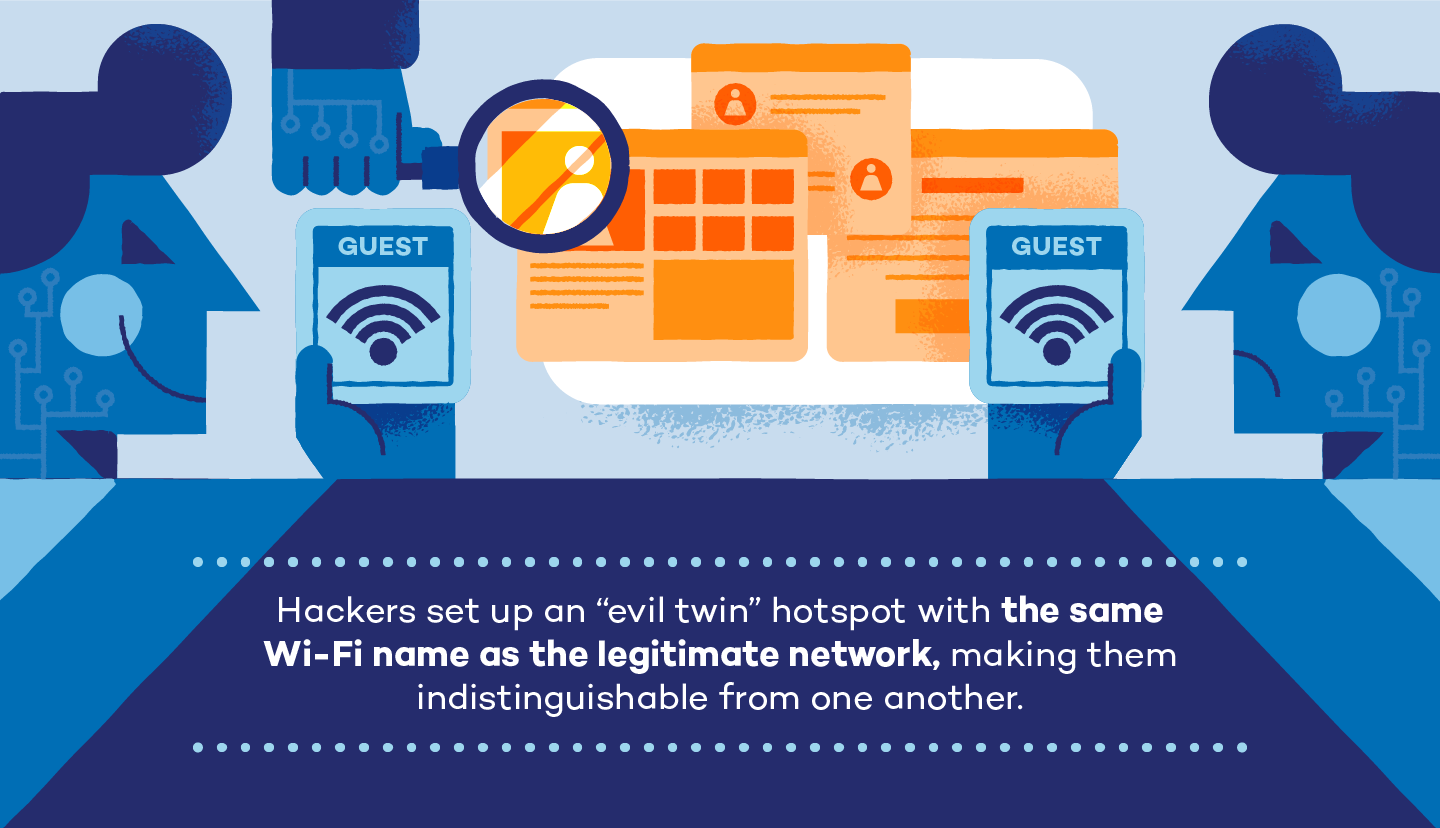
Step 1: Locate a Wi-Fi Target Usually, attackers will find the right place with free and popular Wi-Fi, like some public places — café, libraries, restaurants, etc. How does an evil twin attack work? But there are steps you can take to prevent connection to an evil twin. A VPN is an excellent tool to secure your conversations and financial transactions. If successful, the handshake will be captured and saved in a default location. This can allow them to steal login details, view sensitive information, and potentially further compromise your device.