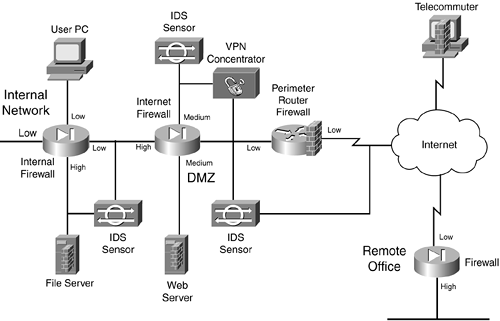
A two-tier firewall is a security system that provides an additional layer of protection for a computer network or system. It is designed to safeguard against unauthorized access and to prevent the spread of malware and other cyber threats.
A two-tier firewall consists of two separate firewall systems that work together to provide protection. The first tier is typically a traditional firewall that is designed to filter traffic based on predetermined rules. It examines incoming and outgoing network traffic and blocks or allows it based on the rules that have been set.
The second tier of a two-tier firewall is usually a host-based firewall. This type of firewall is installed on each individual computer or device in the network and is designed to protect against threats that may bypass the first tier firewall. It monitors and controls inbound and outbound traffic at the host level, providing an additional layer of protection for each device.
One of the main benefits of a two-tier firewall is that it provides a more comprehensive level of protection compared to a single firewall system. By having two separate layers of protection, a two-tier firewall is able to detect and prevent more threats from entering the network. This can be especially important for organizations that handle sensitive data or that are at high risk for cyber attacks.
In addition to providing enhanced security, a two-tier firewall can also improve the overall performance of a network. Because it is able to filter traffic at both the network and host levels, it can help to reduce the amount of unnecessary traffic that is transmitted across the network. This can help to improve the speed and performance of the network, making it more efficient and effective.
Overall, a two-tier firewall is an important tool for protecting a computer network or system against cyber threats. By providing multiple layers of protection, it can help to keep sensitive data safe and prevent the spread of malware and other malicious software. It can also improve the performance of a network, making it more efficient and effective.
Two Tier / Dual Firewall design and best practices

This helps protect against malicious actors who may try to gain unauthorized access to sensitive data or systems. I recently purchased what I intend to become an edge router for controlling access to a DMZ, a VPN, and various other things you would typically put in a DMZ. By keeping up to date with patches, you can ensure that your 2-tier firewall design remains secure and effective against potential threats. This provides routing and firewalling for multiple subnets and locations. By creating different levels of access, you can ensure that users only have access to the resources they need to do their job.
Solved: Two tier firewall design
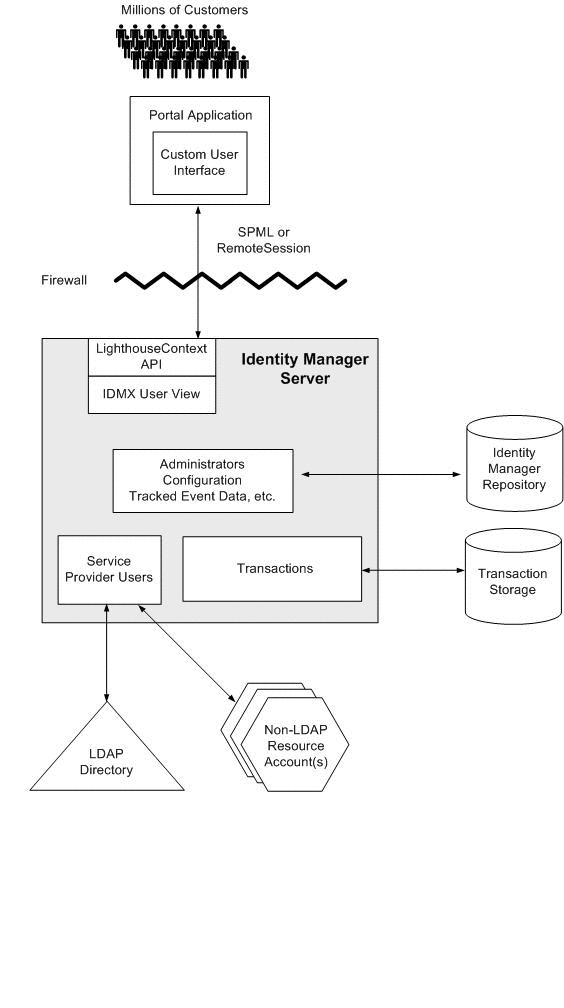
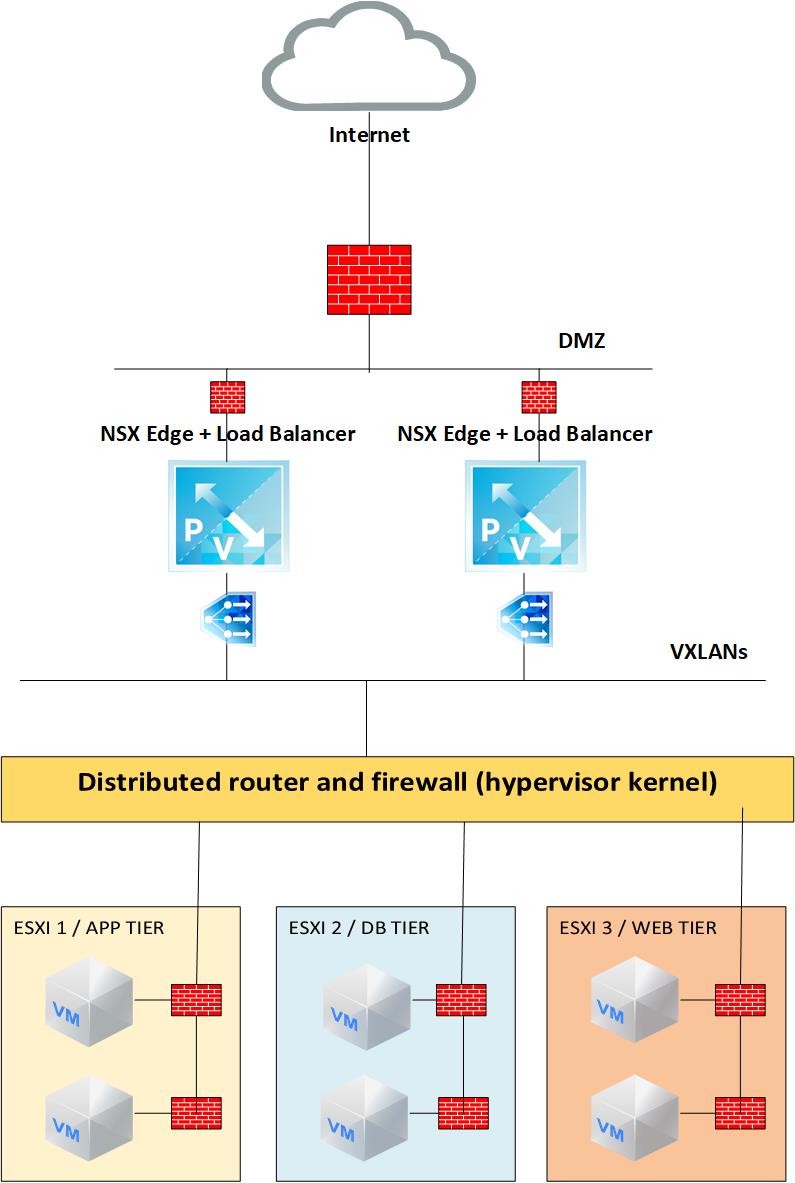
In these types of setups you can basically leave the inner ASA without any NAT configurations and you will mostly be configuring ACLs while the bulk of the firewall configurations are done at the edge devices. So yes, my company has a regulatory requirement for a two tier firewall setup anywhere we choose to have an Internet access point. Specifically, how do I not double-NAT? This includes patching any known vulnerabilities, disabling unnecessary services, and using strong passwords. Topology considerations: physical, virtual, hybrid p-v? By doing this, you can reduce the attack surface of your network and make it more difficult for attackers to gain access. A firewall is a filter that examines packets against a set of defined rules in order to decide whether to allow the packets through. Contribute to the wiki! All incoming packets to IF1 come from the Internet. They could achieve this using packet-filtering firewalls or proxy firewalls.
The difference between a two
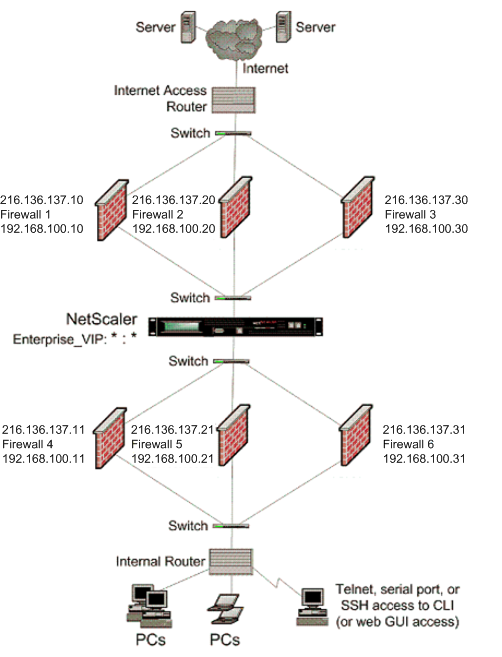
A lot of ISPs use a simple packet filtering firewall, which is acceptable. In my production env. Context based mode is available in Cisco ASA Firewall whereas Checkpoint Firewall has a similar offering which is known as Security Gateway Virtual Edition VE. Separate the network into zones By segmenting the network into different zones, you can create a more secure environment by limiting access to certain areas of the network. Additionally, having multiple firewalls allows you to configure different rulesets on each firewall, which can be used to further restrict access to certain services or applications. Beside above, what is a 3 tier architecture? This could be something like a password and a one-time code sent via text message or email, or a biometric scan such as a fingerprint or facial recognition.

So, if the protected system is a Web server, it should only have TCP port 80 HTTP and, if required, TCP port 443 HTTPS. My reasons are: - I don't like running my edge router virtually on the same hardware that handles my bastion host and VPN - Learning opportunity for static routing, DMZ isolation, etc. How would I prevent that? This includes both the external and internal firewalls, as well as any other devices or applications connected to them. The two hypervisors currently have LAGGs to the 16 port switch, and the switch has a LAGG to the router. Thank you all ahead of time. I really don't think two tier setup is necessary. It would be typically placed towards the top of your rulebase.